Azure’s App Service Plan D1 (Shared) doesn’t allow to use SSL and SNI, so after changed the plan to Basic B1, that support SSL, and now I can install Let’s Encrypt and use it for my blog.
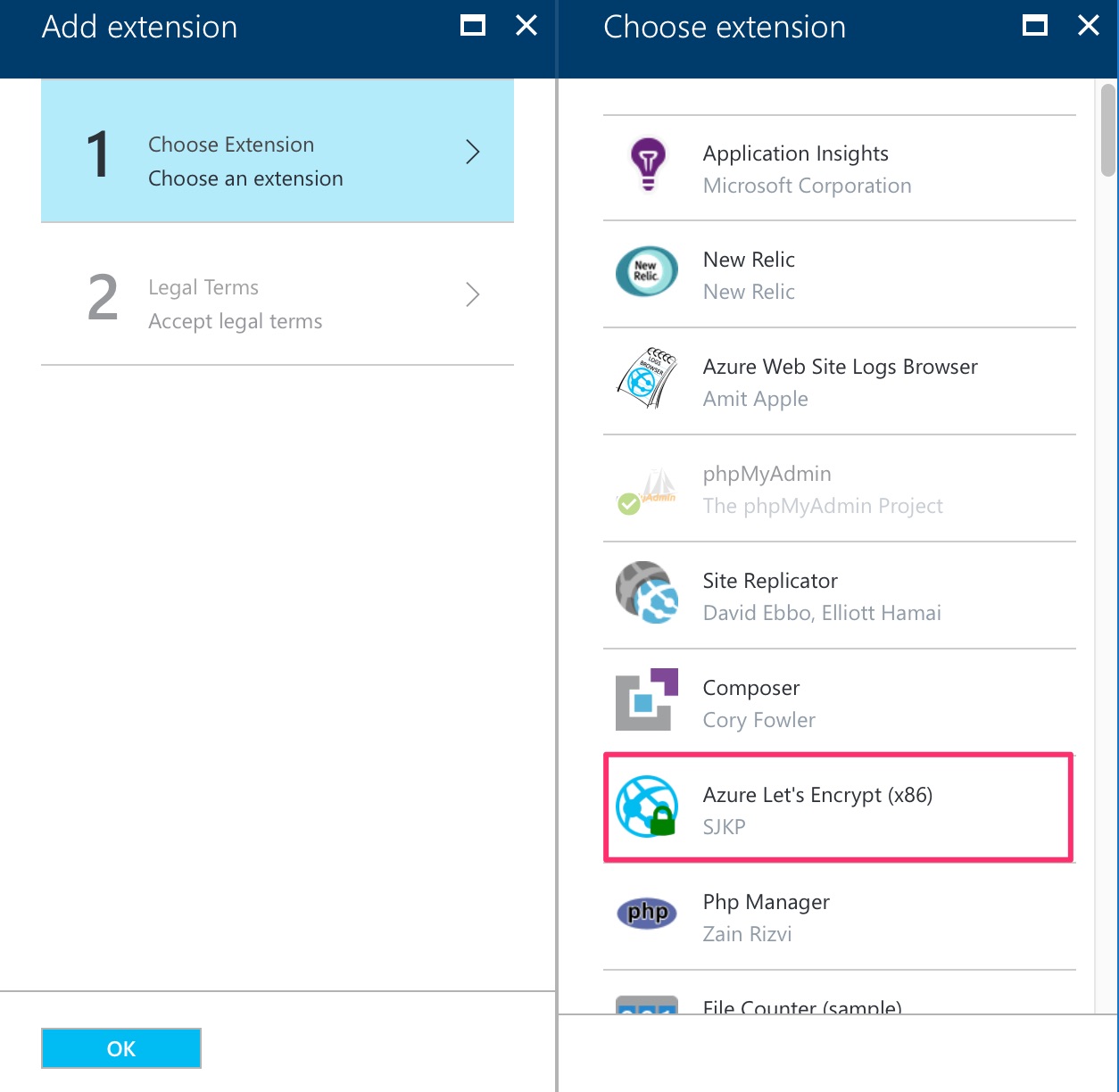
However to setup everything needed for Let’s Encrypt to work and automate the process is tedious, but luckily for the this extension, stuff is easier (read easier, still not as easy as few button clicks). To get the started, get the extension.
Install Azure Let’s Encrypt Extension
Create Table Storage Account
The extension requires uses Azure Web Jobs and it require table storage to work with.
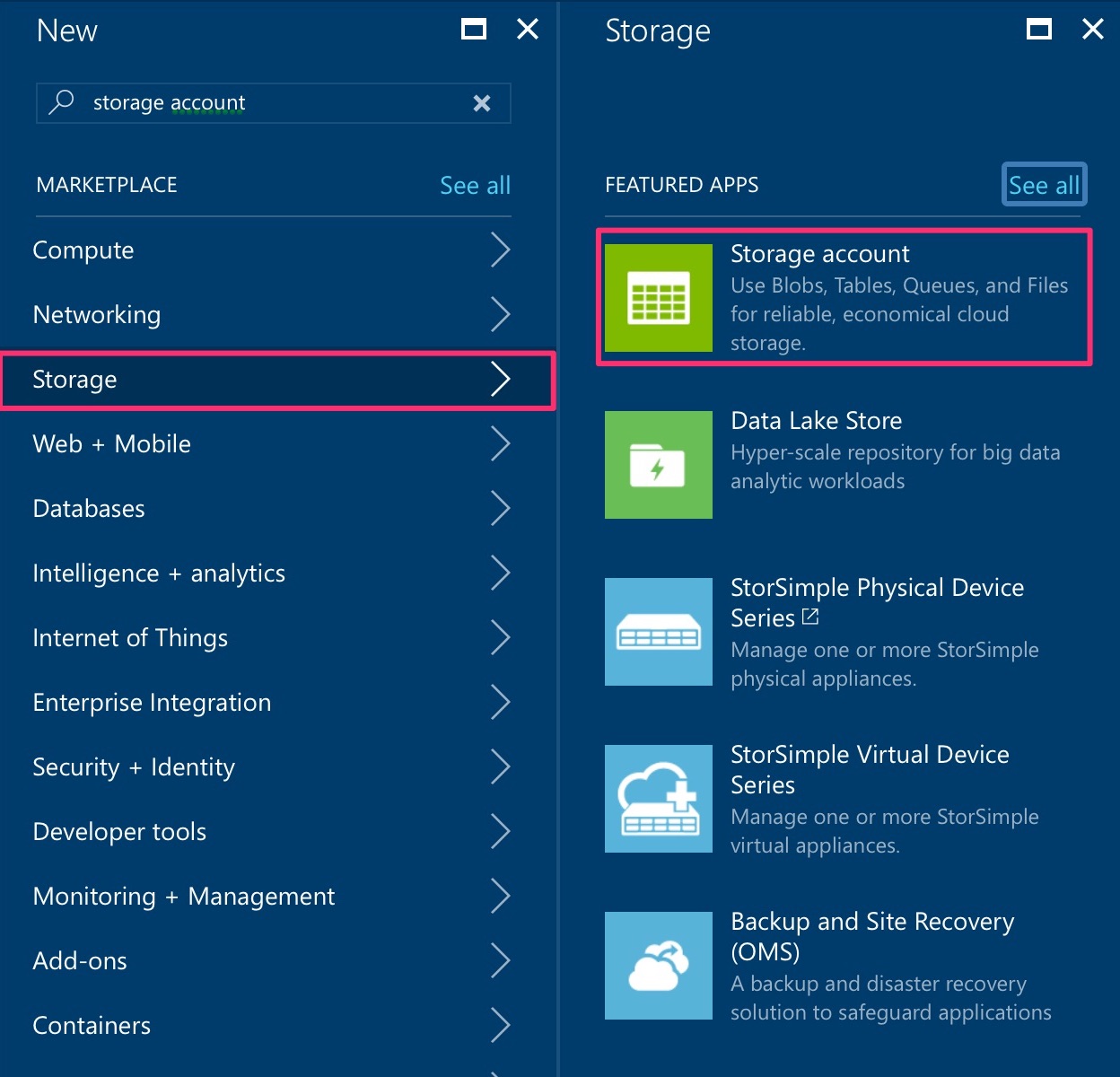
It’s easy to locate, just search in the marketplace.
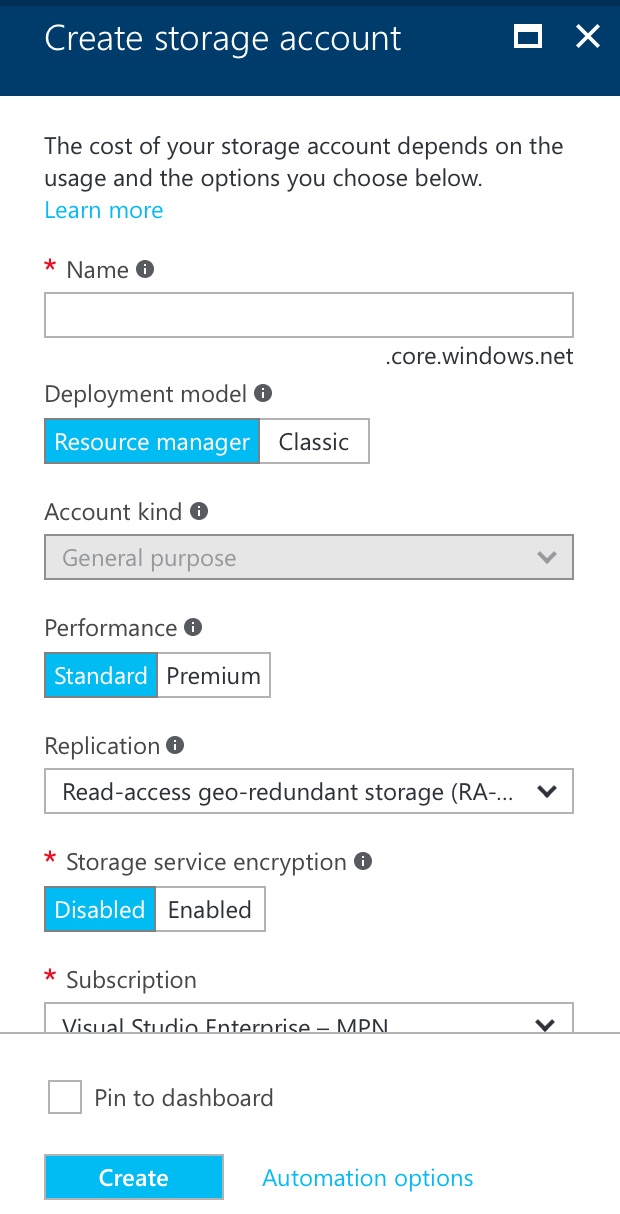
Fill in the usual suspect. Once it’s created, we need to locate the key so that we can set it in our application settings.
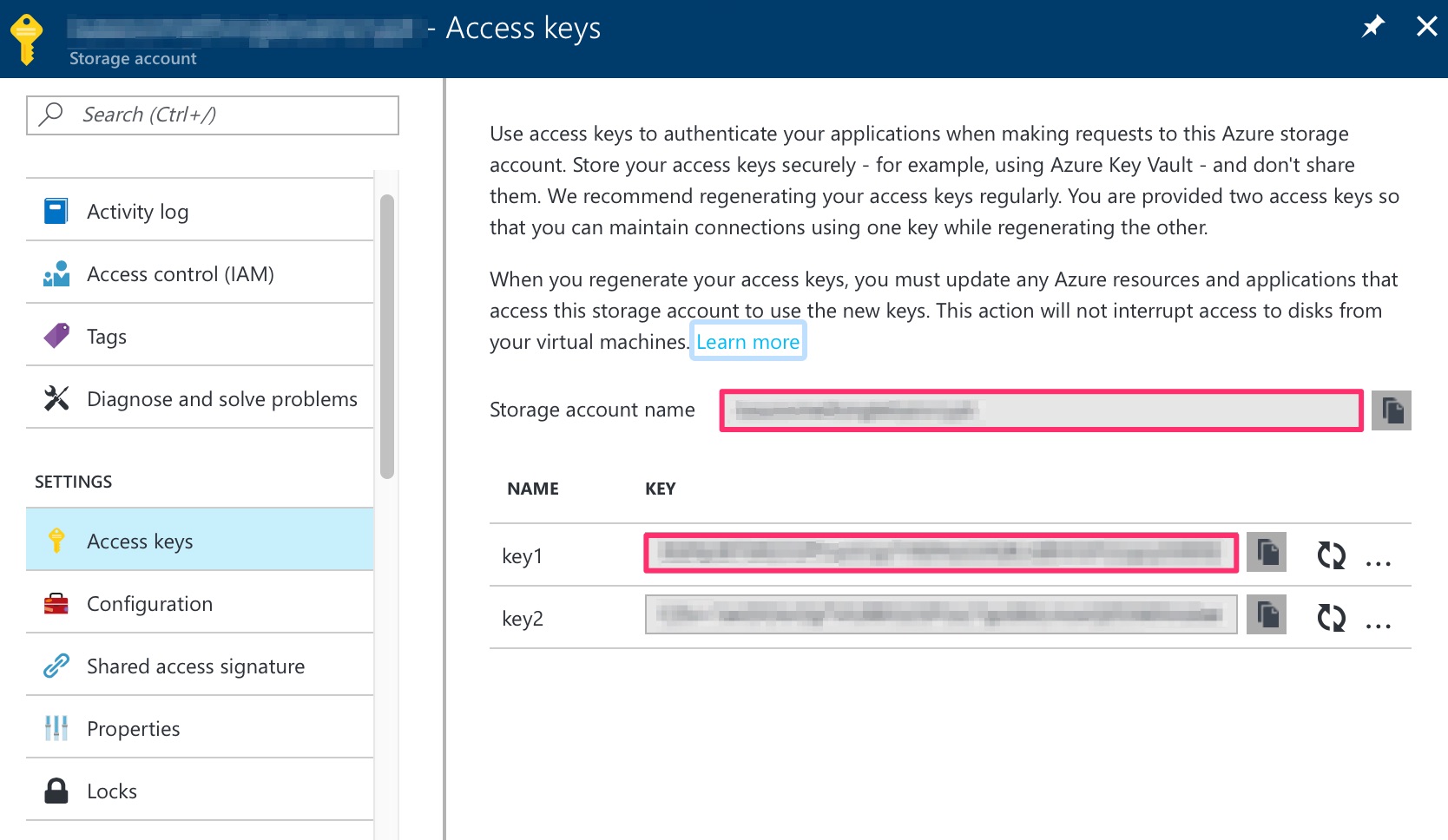
We can locate both storage account name (it’s the one we fill in when creating the account) and key in the Settings > Access keys section.
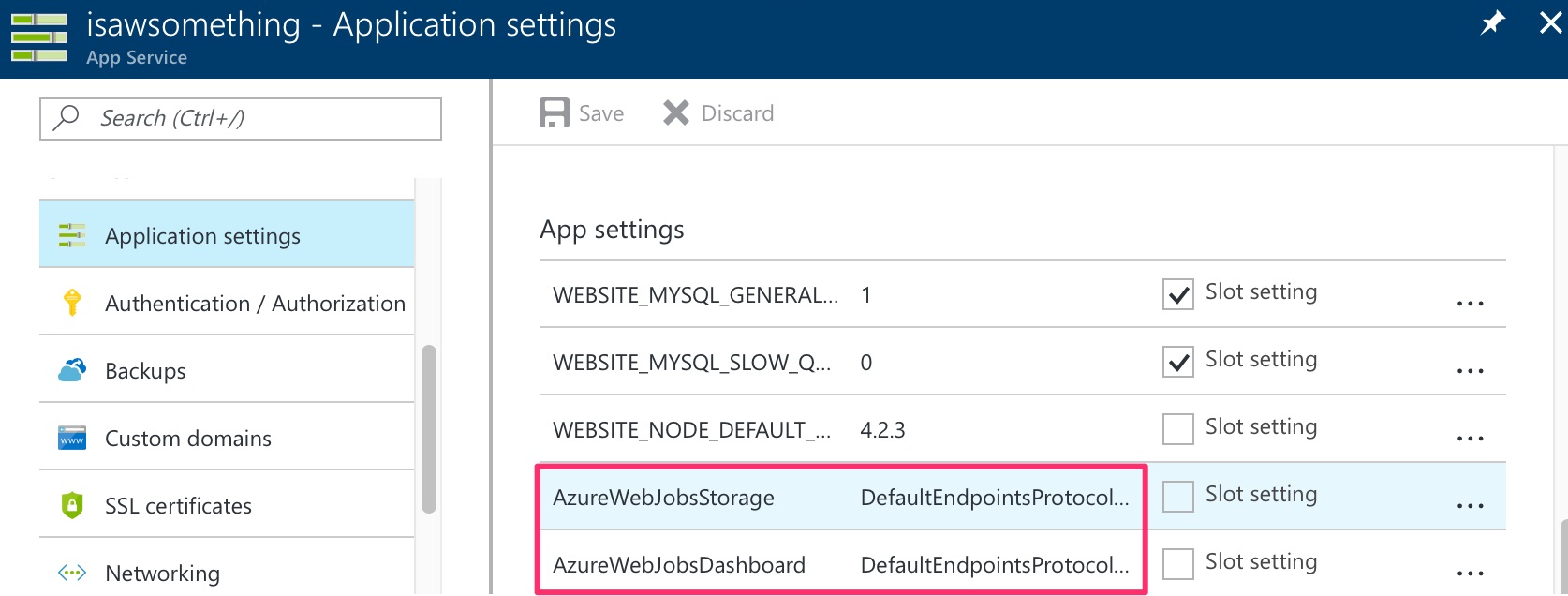
Create 2 keys, AzureWebJobsStorage and AzureWebJobsDashboard, and fill both keys with the same value of DefaultEndpointsProtocol=https;AccountName={storage account name};AccountKey={storage account key}.
Creating Service Principal
We required to create service principal so that the extension can install and update the certificate. They are PowerShell Azure Module around, since I do not have PowerShell on my machine, so I opt for using Azure CLI to configure my Azure. They are couple of ways to install it, I chosen the npm version.
1. Installing Azure CLI
Pretty straight forward, just do npm install -g azure-cli and we’re done.
2. Login to Azure
In terminal, do azure login, you will be given a link and a code, open the link in browser and key in the code, and it will login from the terminal.
3. Create AD application
Run the following in terminal
azure ad app create -n {your new application name} --home-page {url for homepage, I put my home page url here} --identifier-uris {identifier uri} -p {long and strong password here}
After the command is finished, we’ll received status like this:
info: Executing command <b>ad app create</b>
+ Creating application MyAppName
data: AppId: 11111111-1111-1111-1111-111111111111
data: ObjectId: 11111111-2222-3333-4444-555555555555
data: DisplayName: MyAppName
data: IdentifierUris: 0=http://www.myidentifier.com
data: ReplyUrls:
data: AvailableToOtherTenants: False
data: HomePage: http://www.stephensaw.me
info: ad app create command OK
4. Create Service Principal
From previous command’s output, we can get the AppId, we’ll need it for this command. azure ad sp create -a {AppId from previous command}. After running this command we’ll receive another status something like this:
info: Executing command <b>ad sp create</b>
+ Creating service principal for application 11111111-1111-1111-1111-111111111111
data: Object Id: 22222222-2222-2222-2222-222222222222
data: Display Name: isawsomething
data: Service Principal Names:
data: 11111111-1111-1111-1111-111111111111
info: ad sp create command OK
We need to note down the
5. Assign Contributor role to the Service Principal
With the ObjectId we get from previous command output, execute this azure role assignment create --objectId {object id given by previous command} -o Contributor -c /subscriptions/{azure subscription id}/.
Configure Azure Let’s Encrypt Extension
We’re almost there, now we only left the simple part. Go to the extension’s configuration page via opening in SCM site or clicking browse from the installed extension.
We’ll see some configuration details and their explanation from the extension’s page.
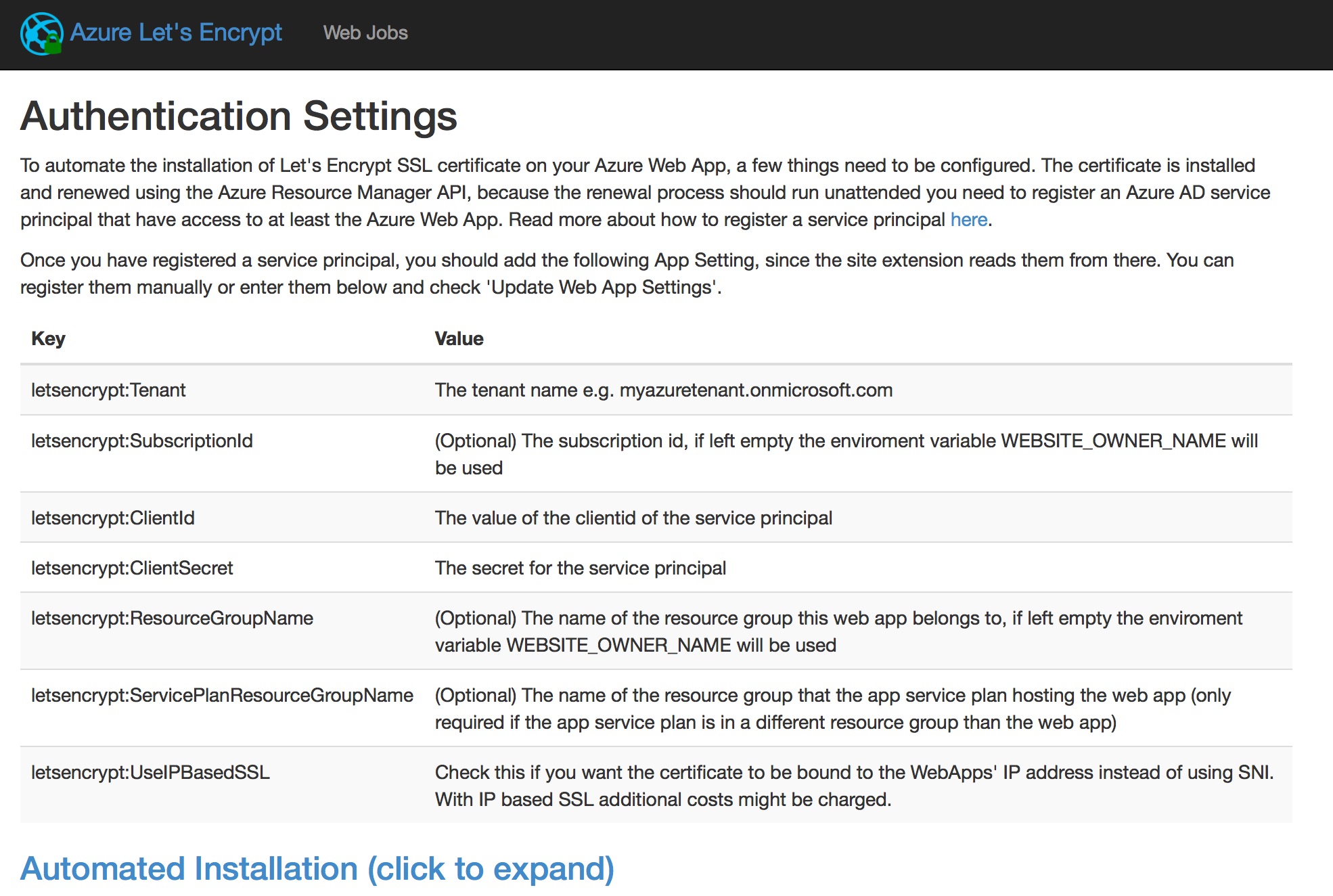
When we’re ready to configure, scroll to the bottom of the page and fill in the related.
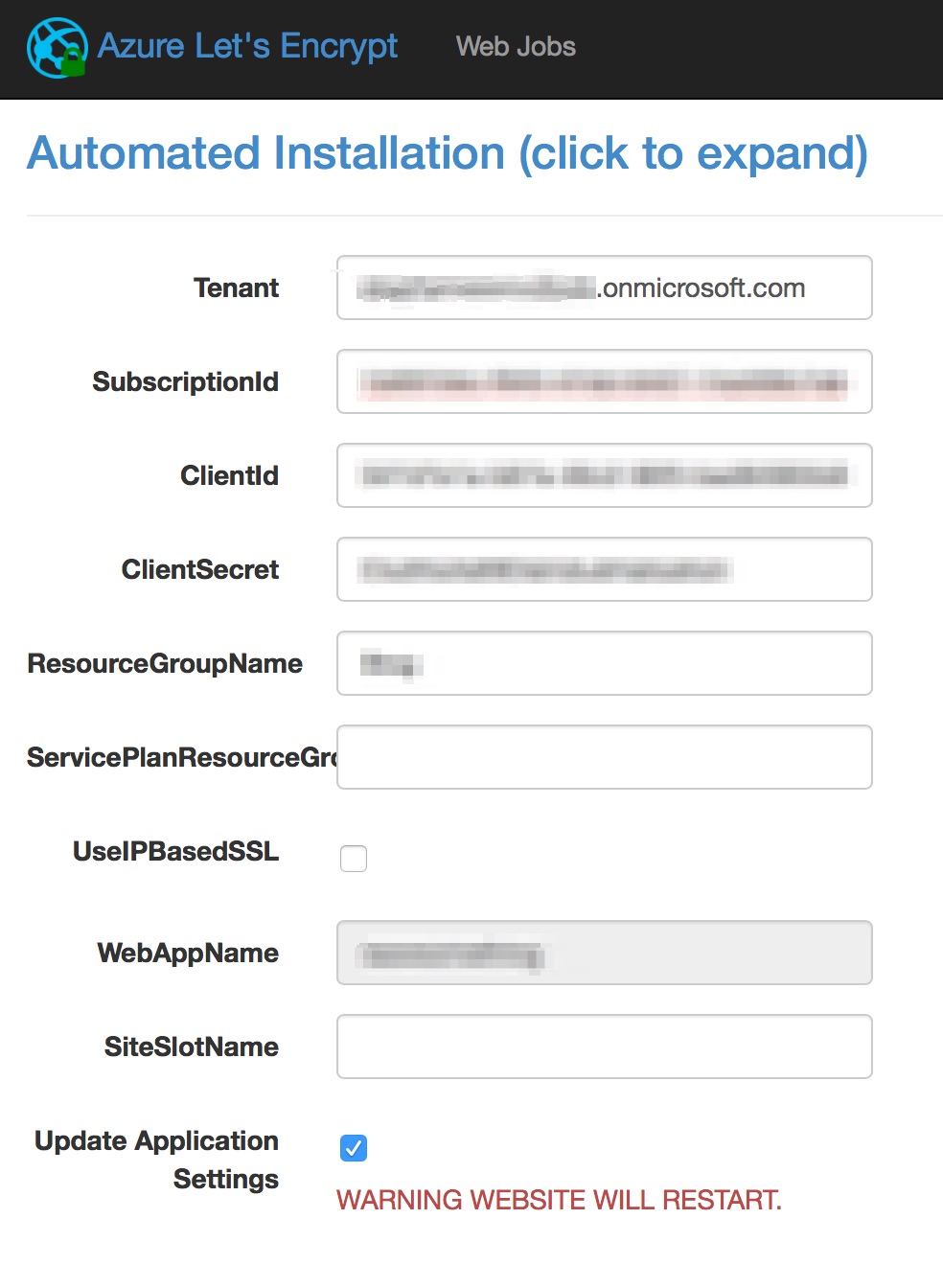
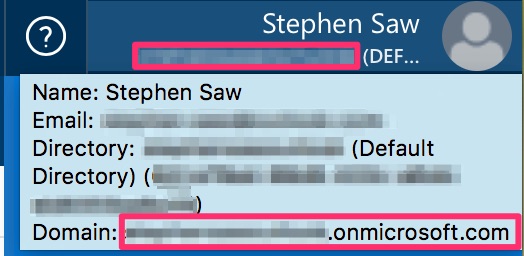
The Tenant is the *.onmicrosoft.com value. To get that, in Azure portal, click on the logged in user on top right corner, or mouse hover to review more information in a tooltip.
The ClientId is the AppId we get when we execute the azure ad app create command, while the ClientSecret is the password we key in when execute the azure ad app create.
Request for Certificate
After configured the extension, we finally get to last page before we can request certificate.
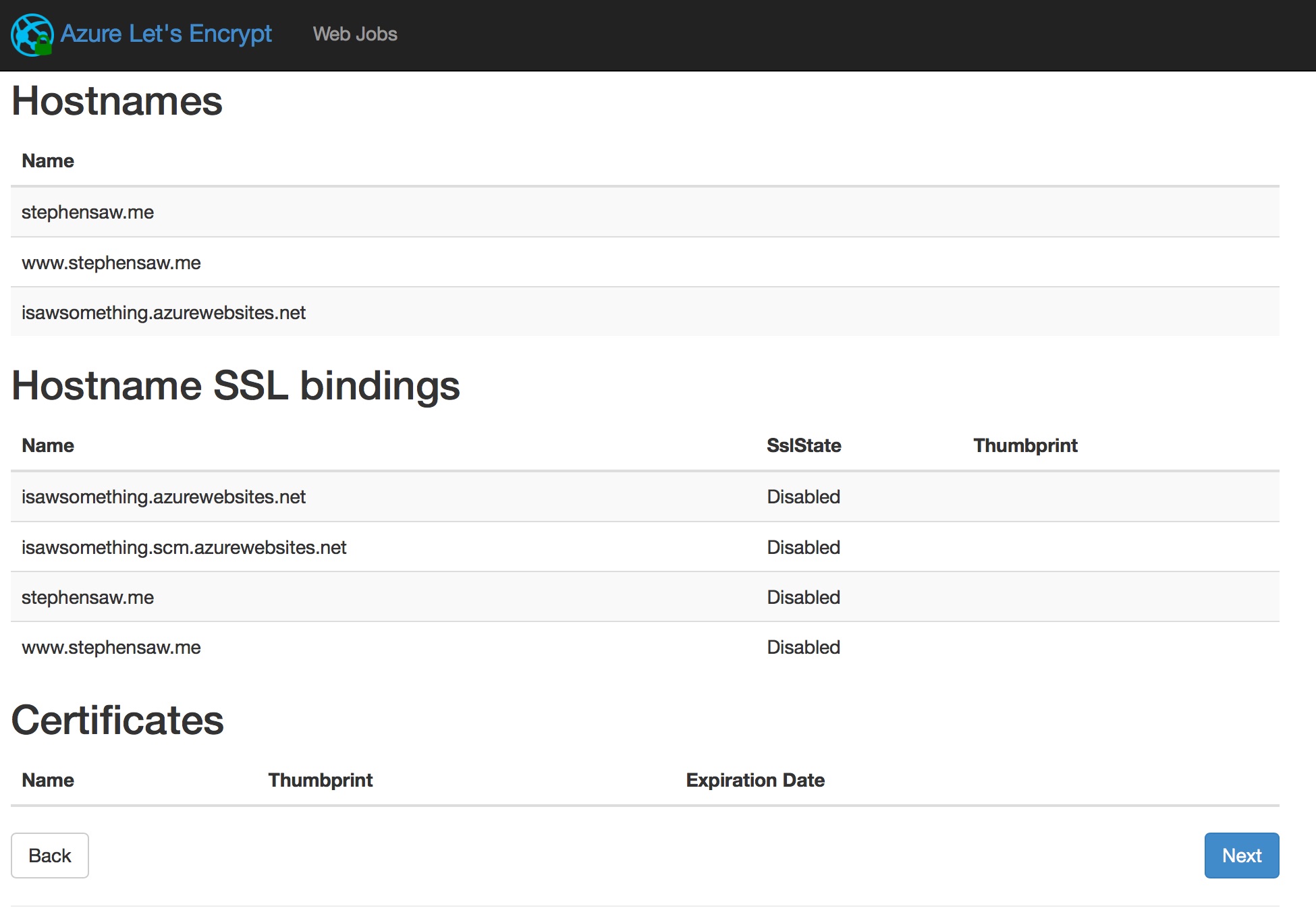
Clicking the Next button will bring us to the request certificate page.
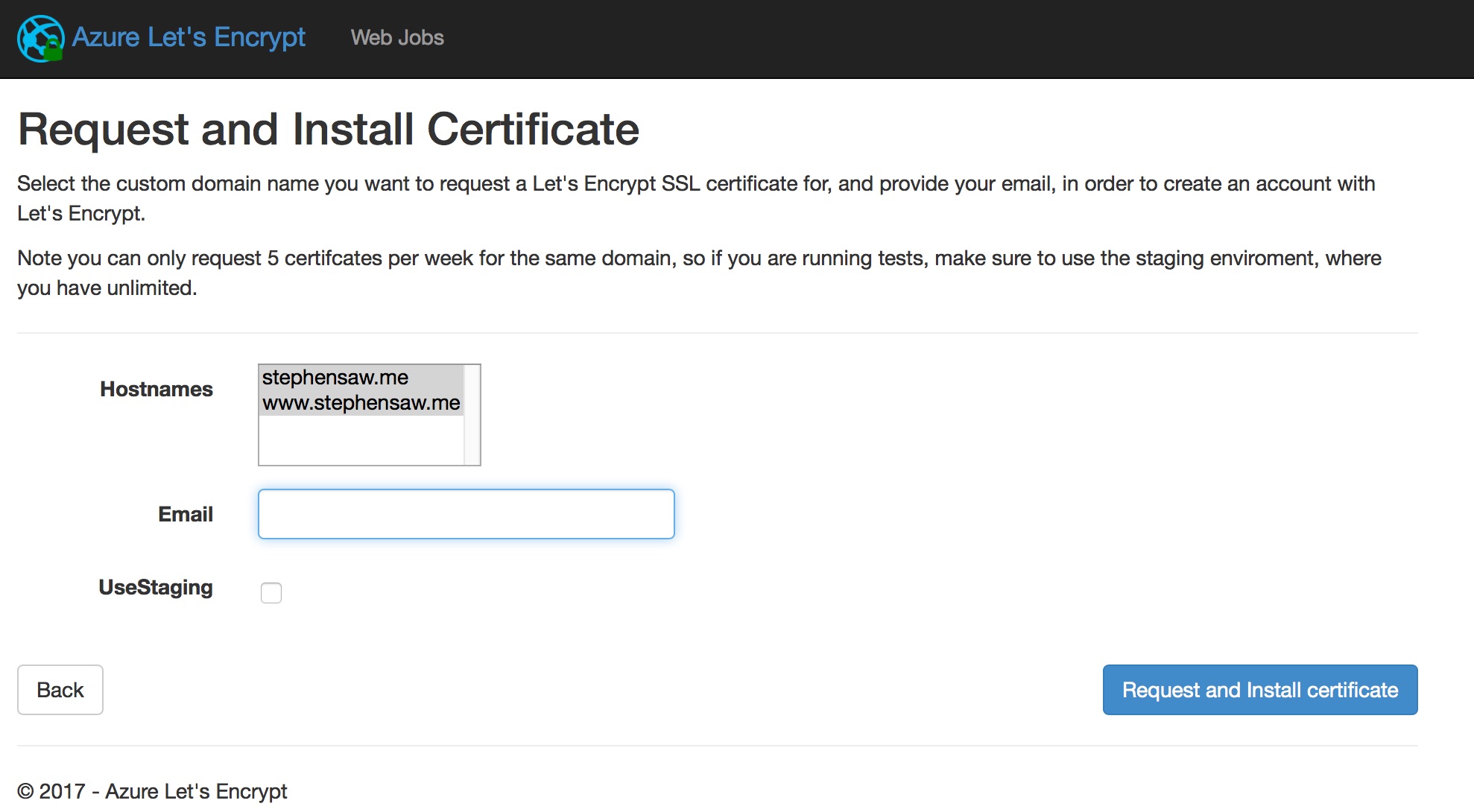
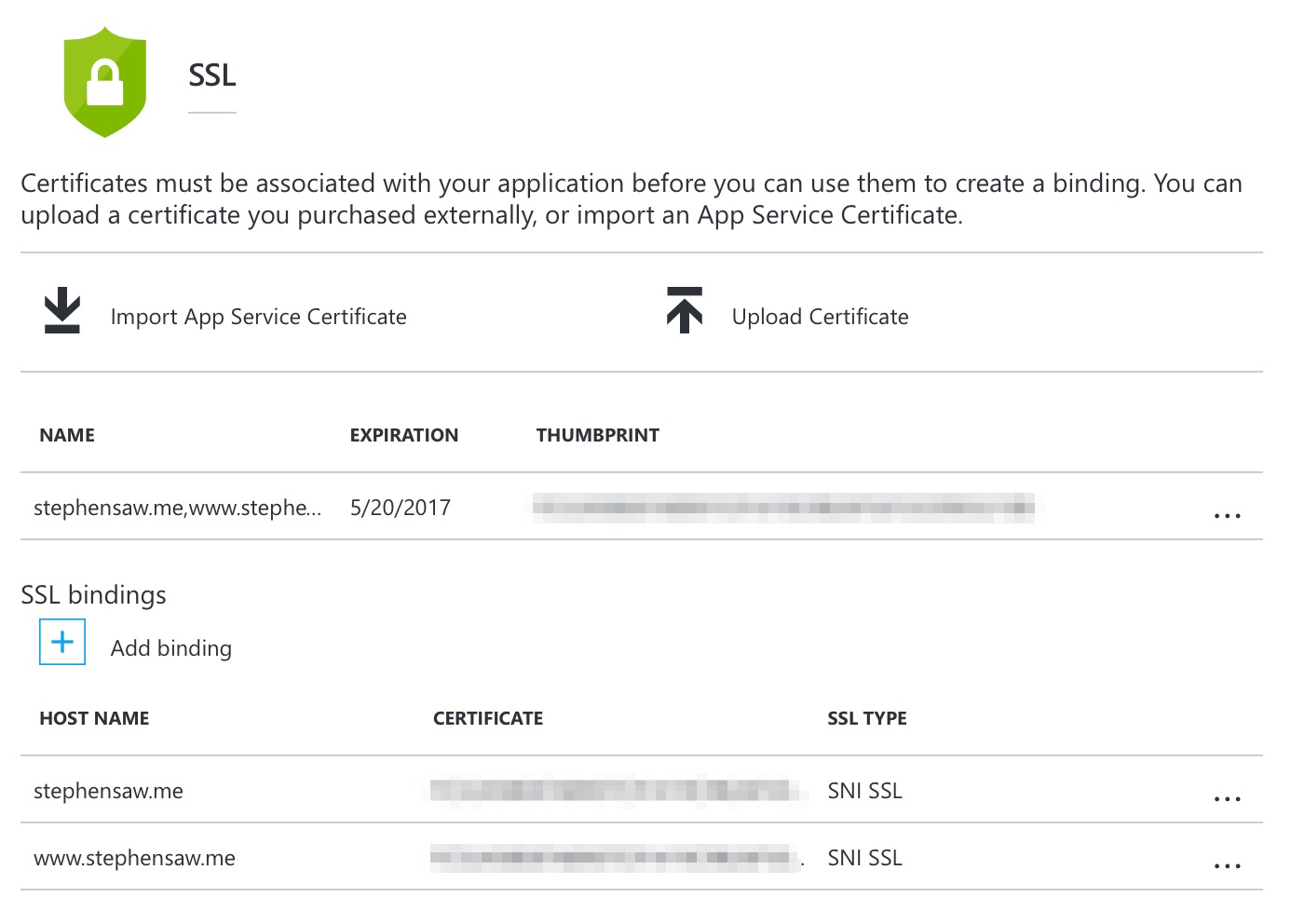
Of course, we’ll need to have our custom domain for that. Clicking that last blue button Request and Install certificate and wait to reap the result of our hardwork.
We can see that our certificate been configured.
Source: could not done it without reading this helpful tutorial.